Cyber IT Security
Đối tác đáng tin cậy của bạn trong các giải pháp an ninh mạng trong thế giới số hóa, việc bảo vệ doanh nghiệp của bạn khỏi các mối đe dọa mạng quan trọng hơn bao giờ hết. Cyber IT Security, chúng tôi cung cấp các dịch vụ an ninh mạng toàn diện được thiết kế riêng để bảo vệ tổ chức của bạn từ trong ra ngoài.
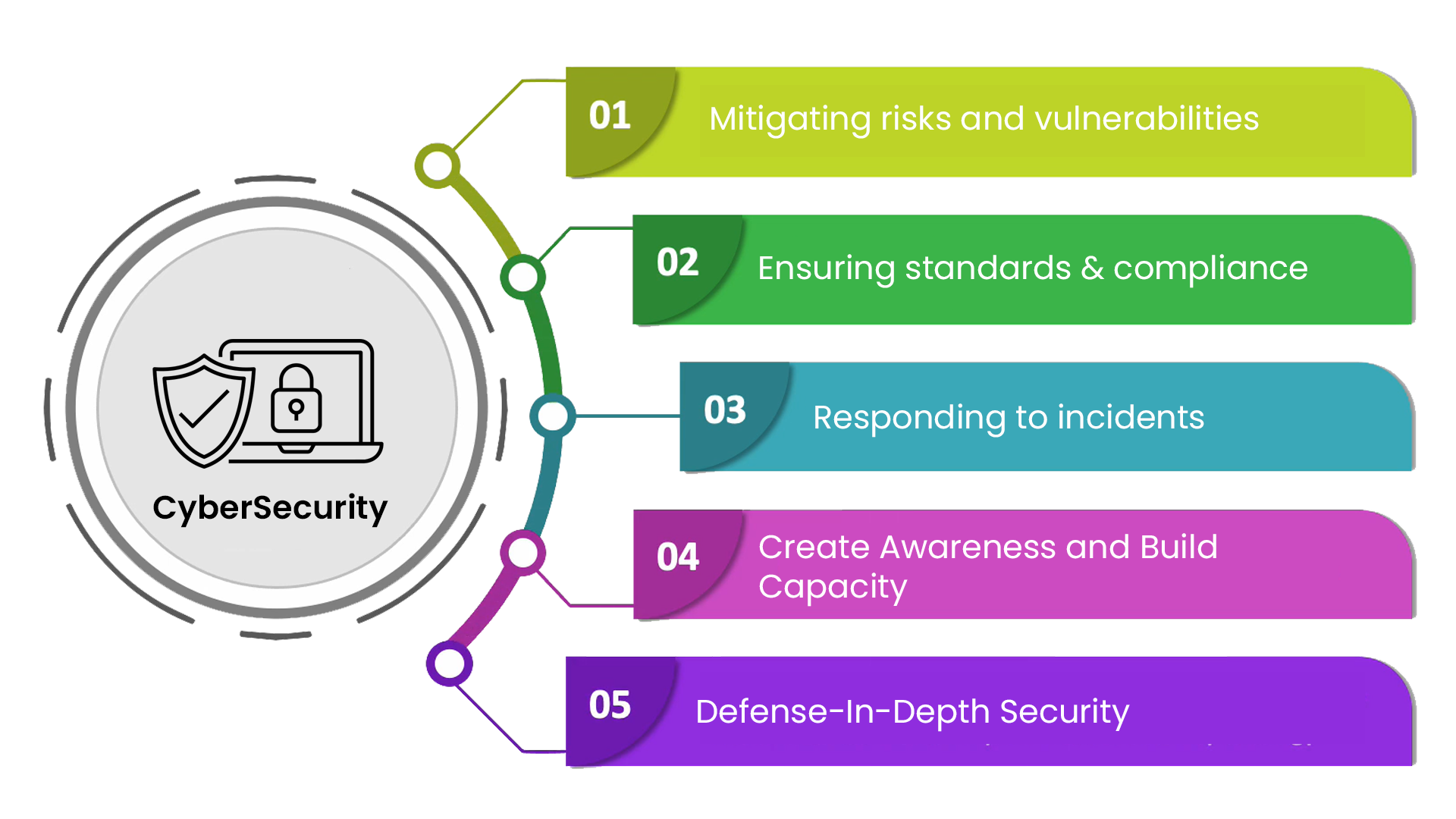
Giải pháp An toàn Thông tin toàn diện
Không chỉ ISO 27001 – Chúng tôi tư vấn triển khai hệ thống bảo mật theo ISO 27017, 27018, 27701, NIST và tiêu chuẩn theo yêu cầu doanh nghiệp
Tư vấn miễn phíCyber IT Security khác biệt như thế nào?
Chuyên gia hàng đầu
ISO 27001 Lead Auditor, CISA, PMP – hơn 20 năm tư vấn, triển khai bảo mật cho doanh nghiệp
Hệ thống vận hành thực tế
Không chỉ xây dựng hồ sơ đạt chứng nhận – mà thiết lập hệ thống an toàn CNTT hoạt động hiệu quả và kiểm soát rủi ro thực sự
Tuỳ chỉnh theo yêu cầu
Tư vấn triển khai hệ thống theo ISO 27001, 27017, 27018, 27701, NIST SP 800… hoặc theo yêu cầu đặc thù từng ngành












Dịch vụ của chúng tôi?
Đánh giá lỗ hổng bảo mật
- Đánh giá lỗ hổng là quá trình xác định và đánh giá các điểm yếu bảo mật tiềm ẩn trong hệ thống, mạng hoặc ứng dụng để xác định mức độ rủi ro mà chúng gây ra cho tổ chức.
Kiểm tra thâm nhập
- Kiểm thử thâm nhập là quá trình đánh giá tính bảo mật của hệ thống máy tính hoặc mạng bằng cách mô phỏng cuộc tấn công từ kẻ xấu để xác định các lỗ hổng và điểm yếu có thể bị khai thác.
Đánh giá bảo mật và tuân thủ
- Kiểm toán bảo mật và tuân thủ là tiêu chuẩn được công nhận trên toàn cầu để tạo, triển khai, duy trì và cải thiện hệ thống quản lý bảo mật thông tin (ISMS) trong một tổ chức.
Đánh giá cơ sở hạ tầng CNTT
- Đánh giá toàn diện về cơ sở hạ tầng công nghệ của một tổ chức, bao gồm phần cứng, phần mềm, mạng và trung tâm dữ liệu, nhằm đánh giá tính hiệu quả, hiệu suất và bảo mật của tổ chức đó.
Đánh giá ứng dụng
- Kiểm tra ứng dụng (Trang web / Cổng thông tin nội bộ / Ứng dụng di động) là quá trình xem xét và đánh giá tính bảo mật, chức năng và hiệu suất của ứng dụng để xác định và giảm thiểu các rủi ro và lỗ hổng tiềm ẩn.
Bảo vệ an ninh mạng toàn diện
-
Phát hiện và ứng phó mối đe dọa
Chủ động xác định và giảm thiểu các mối đe dọa mạng bằng hệ thống giám sát tiên tiến và giao thức ứng phó nhanh của chúng tôi. -
Quản lý rủi ro và tuân thủ
Điều hướng bối cảnh phức tạp của các quy định về an ninh mạng với các giải pháp tuân thủ và hướng dẫn chuyên môn của chúng tôi. -
Bảo vệ dữ liệu và quyền riêng tư
Đảm bảo tính bảo mật, toàn vẹn và khả dụng của dữ liệu quan trọng của bạn bằng các biện pháp mã hóa và quyền riêng tư mạnh mẽ. -
Đánh giá bảo mật và kiểm tra thâm nhập
Phát hiện lỗ hổng trước khi chúng có thể bị khai thác thông qua các cuộc kiểm tra bảo mật và kiểm tra thâm nhập toàn diện của chúng tôi.
Tại sao chọn chúng tôi?
Chuyên môn. Kinh nghiệm. Xuất sắc.
-
Chuyên gia được chứng nhận
Đội ngũ của chúng tôi bao gồm các chuyên gia an ninh mạng được chứng nhận quốc tế, tận tâm bảo vệ tài sản kỹ thuật số của bạn. -
Giải pháp tùy chỉnh
Chúng tôi hiểu rằng mỗi tổ chức đều là duy nhất. Các giải pháp của chúng tôi được tùy chỉnh để đáp ứng nhu cầu bảo mật cụ thể của bạn. -
Thành tích đã được chứng minh
Với nhiều năm kinh nghiệm và danh mục khách hàng hài lòng, Cyber IT Security là cái tên đáng tin cậy trong lĩnh vực an ninh mạng. -
Hỗ trợ 24/7
Các mối đe dọa mạng không bao giờ ngừng nghỉ, và chúng tôi cũng vậy. Đội ngũ hỗ trợ của chúng tôi luôn sẵn sàng hỗ trợ bạn suốt ngày đêm.
Các ngành công nghiệp chúng tôi phục vụ
Bảo mật tùy chỉnh cho mọi lĩnh vực
Cho dù bạn làm việc trong lĩnh vực tài chính, chăm sóc sức khỏe, giáo dục hay bất kỳ ngành nào khác, Cyber IT Security đều có chuyên môn để bảo vệ thông tin nhạy cảm và cơ sở hạ tầng quan trọng của bạn.
Bắt đầu ngay hôm nay
Bảo vệ doanh nghiệp của bạn với An ninh CNTT mạng
Đừng đợi cho đến khi quá muộn. Hãy liên hệ với chúng tôi ngay hôm nay để được tư vấn và thực hiện bước đầu tiên hướng tới một tương lai an toàn hơn.
Bạn đã sẵn sàng bảo vệ hệ thống khỏi tấn công mạng?
Tải ngay checklist ISO 27001 để đánh giá mức độ sẵn sàng và nhận tư vấn chiến lược phù hợp với doanh nghiệp bạn.
Tải checklist miễn phíLiên hệ
Hỗ trợ - tư vấn
+84 377 338 223
Chúng tôi luôn sẵn sàng hỗ trợ kỹ thuật qua điện thoại hoặc email 24/7.
Chúng tôi có thể tư vấn trao đổi trực tiếp, qua điện thoại hoặc email từ 8 giờ sáng đến 18 giờ tối, từ Thứ Hai đến Thứ Sáu.